Security – Standard IEEE 802.1X
The CS141 establishes new security standards
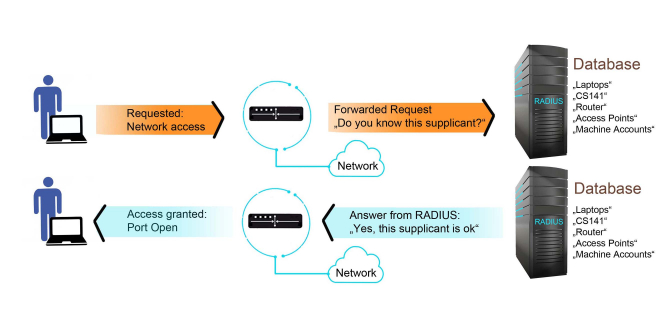
Break-ins into semi-open or not fully closed networks have always been one of the biggest problems for system administrators: As soon as a user is allowed to log on to a network with their given device, they establish basic access to the infrastructure points whose IP addresses are known. Thus, it follows logically that first line of defense for such break-ins the exercise of discernment as to which network-enabled device ought to be allowed access to the network, regardless of its user.
It’s of course understandable that a company wants to deny unchecked private devices access to its own protected intranet. However, this becomes more and more difficult to enforce as the number of employees and computers in the company increases. The simplest solution here is to simply “lock out” unauthorized hardware from the system via IEEE 802.1X: a device that does not meet the access criteria is not assigned a port, and without an open port there is no way to penetrate a network.