What can one do with RADIUS on a CS141/BACS?
RADIUS (Remote Authentication Dial-In User Service) is widely used in modern IT. This service makes it relatively easy to authenticate and authorize users wishing to log into a network from a location outside the network itself. As such, RADIUS can also be used, for example, if you want to bill certain services according to usage time (accounting), or manage company WLAN access in a quick and efficient manner.
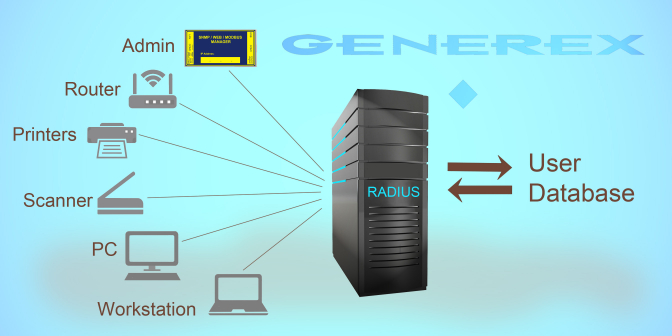
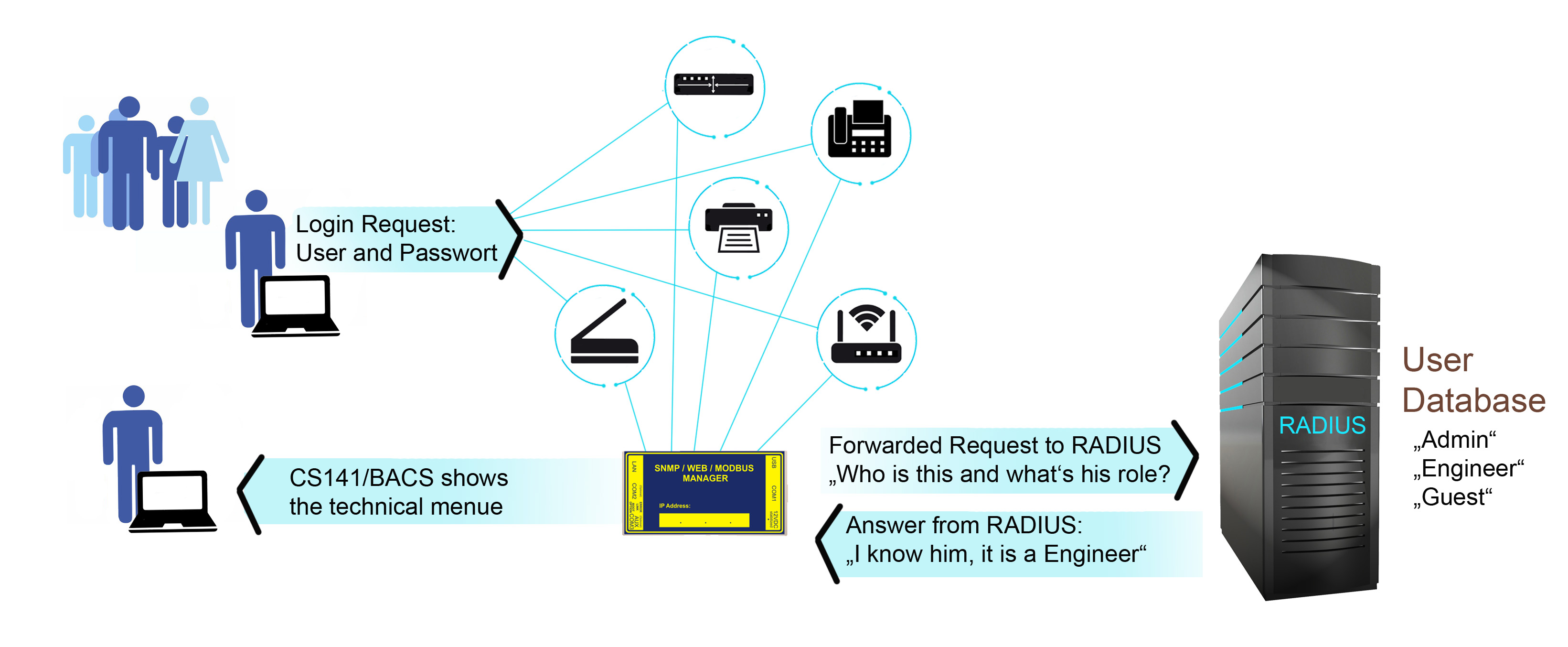
For the CS141/BACS, RADIUS primarily plays a role in dynamic password management or direct network access based on LAN access. A CS141/BACS offers central user management via dynamic password management and displays exactly the menus that an administrator has intended for the user.