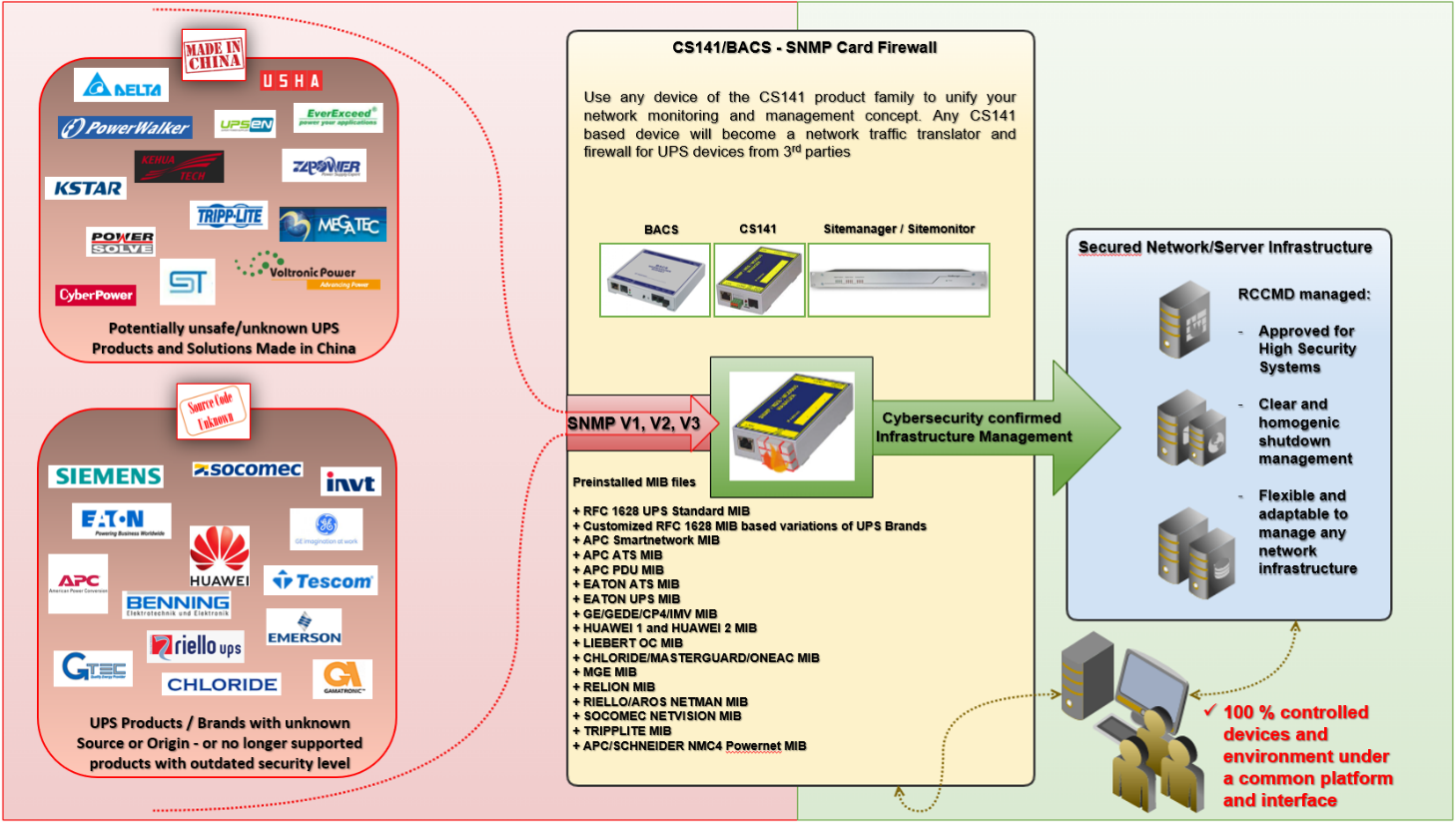
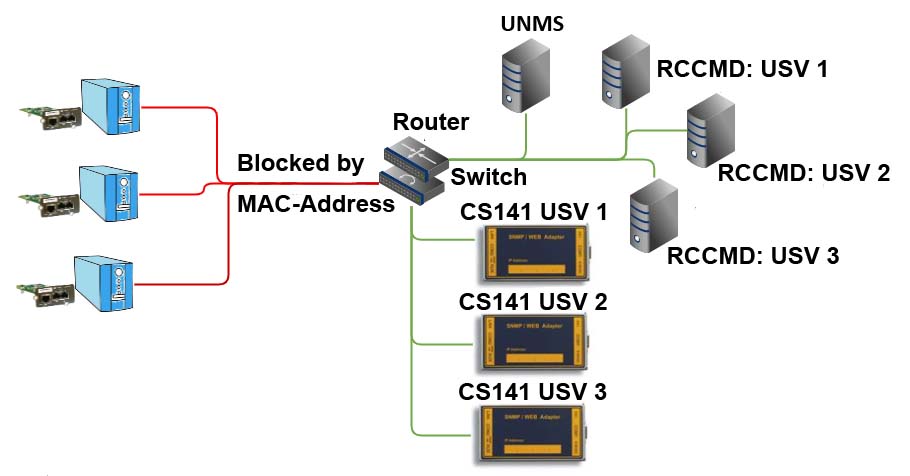
The CS141 as a gateway for UPS network devices and data
Every time another hacker attack story hits the media, the discussion around how to secure a high-security network against "malware / ransomware" reaches a new fever pitch -- and the resulting discovery always seems to be that under certain conditions, essential elements of an infrastructure are inextricably linked to network access:
How is one supposed to query an integrated UPS SNMP card with firmware from a source that is not 100% verifiable without using the device’s LAN port?
It’s a problem that is becoming increasingly important in the highly sensitive area of power supply: no server system can be expected to succeed without a functioning mains power concept. Experience shows that attacks are increasingly targeting precisely this infrastructure.
Firmware that could otherwise be assumed to negatively influence system integrity and security and which is designated as such by watchdog / government agencies does not give a good feeling of security per se – and such a flaw exists as such with all devices “made in China”. In addition, with an increasing number of different hardware options and configurations, each company wants to offer or pre-install its own biotope of "query and control software", which quickly makes the number of clients and software tools in the network confusing and otherwise overly complex. As a result, numerous individual ports have to be opened in the network, which can in turn serve to open up more gateways for hackers.